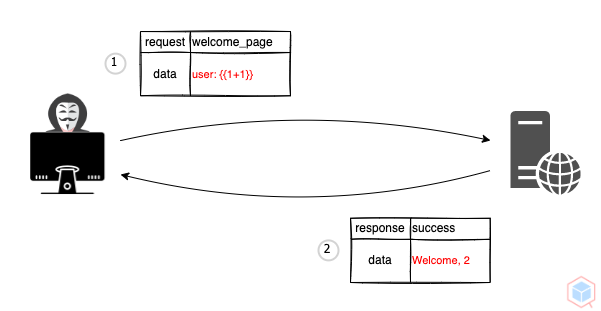
A threat actor may use a native template syntax on the vulnerable target to execute commands
- Threat actor sends a native template syntax to a vulnerable target that uses a template engine
- The target process the syntax and executes the result
@app.route('/welcome', methods=['GET'])
def welcome():
user = request.args.get('user')
template = f"<h1>Welcome, {user}!</h1>"
return render_template_string(template){{1+1}}
Welcome, 4
High
- Server Side Template Injection
- SST injection
- Command execution
- Input validation
- Logic-less
E0679353-0BB6-404B-A6CC-6F6305FF118C