Releases: ory/hydra
v2.2.0
Ory Hydra, the OAuth2 and OpenID Connect server designed for web-scale deployments introduces over 6x higher OAuth2 throughput on a single PostgreSQL instance!
Want to check out Ory Hydra yourself? Try common OAuth2 flows in the Ory OAuth2 Get Started guide!
This version significantly enhances performance, processing over 6x more authorization flows than version 2.1, thanks to architectural improvements that minimize database interactions for login and consent processes.
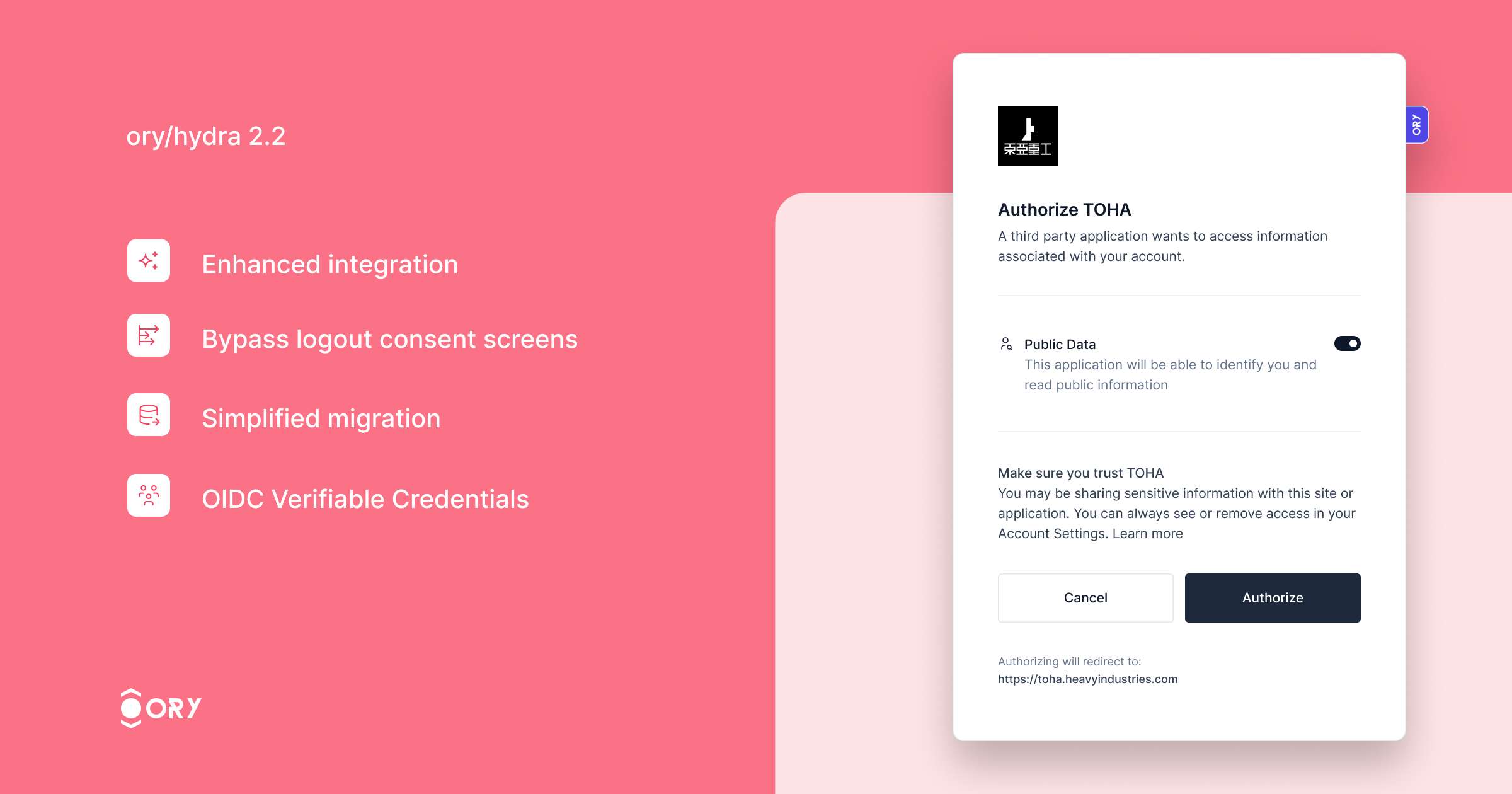
Key improvements include:
- Enhanced integration with Ory Kratos, ensuring seamless synchronization of login and logout states across both services. Users logged out from Ory Hydra will automatically log out from Ory Kratos, enhancing security and user experience.
- The ability to bypass the logout consent screen for specific clients, streamlining the logout process.
- Simplified migration with the new feature to import OAuth2 Client IDs, making the transition to Ory Hydra smoother.
- Support for the OIDC Verifiable Credentials specification, expanding the server's capabilities in identity verification.
Thank all contributors who have made this release available!
Bug Fixes
-
Return empty slice if requested_scope or audience is null (#3711) (65165e7)
-
Correct id token type in token exchange response (#3625) (d1f9ba8):
Closes ory/client-go#2
-
Handle subject mismatch gracefully (#3619) (af0d477):
We now redirect to the original request URL if the subjects between
the remembered Hydra session and what was confirmed by the login
screen does not match. -
Handle token hook auth config (#3677) (1a40833):
- fix: handle token hook auth config
- fix: bump golangci-lint
-
Incorrect down migration (#3708) (8812e0e), closes /github.com/ory/hydra/pull/3705#discussion_r1471514014
-
Timeout in jwt-bearer grants when too many grants are available (#3692) (a748797)
-
Deflake ttl test (6741a49)
-
Only query access tokens by hashed signature (a21e945)
-
Reject invalid JWKS in client configuration / dependency cleanup and bump (#3603) (1d73d83)
-
Restore ability to override auth and token urls for exemplary app (#3590) (dfb129a)
-
Return proper error when the grant request cannot be parsed (#3558) (26f2d34)
Documentation
Features
-
Add prompt=registration (#3636) (19857d2):
Ory Hydra now supports a
registrationvalue for thepromptparameter of
the authorization request. When specifyingprompt=registration, Ory Hydra
will redirect the user to the URL found underurls.registration
(instead ofurls.login). -
Add skip_logout_consent option to clients (#3705) (2a653e6):
Adds a special field which disables the logout consent screen when performing OIDC logout.
-
Re-enable legacy client IDs (#3628) (5dd7d30):
This patch changes the primary key of the
hydra_clienttable. We do not expect issues, as that table is probably not overly huge in any deployment. We do however highly recommend to test the migration performance on a staging environment with a similar database setup. -
Remove flow cookie (#3639) (cde3a30):
This patch removes the flow cookie. All information is already tracked in the request query parameters as part of the {login|consent}_{challenge|verifier}.
-
Remove login session cookie during consent flow (#3667) (5f41949)
-
Add more resolution to events and collect client metrics (#3568) (466e66b)
-
Add state override (b8b9154)
-
Add support for OIDC VC (#3575) (219a7c0):
This adds initial support for issuing verifiable credentials
as specified in https://openid.net/specs/openid-connect-userinfo-vc-1_0.html.Because the spec is still in draft, public identifiers are
suffixed withdraft_00. -
Allow to disable claim mirroring ([#3563](https:...
v2.2.0-rc.3
Introduces logout compatibility with Ory Kratos.
Bug Fixes
- Add exceptions for internal IP addresses (#3608) (1f1121c)
- Add kid to verifiable credential header (#3606) (9f1c8d1)
- Deflake ttl test (6741a49)
- Docker build (#3609) (01ff9da)
- Enable CORS with hot-reloaded origins (#3601) (6f592fc)
- Only query access tokens by hashed signature (a21e945)
- Racy random string generation (#3555) (1b26c4c)
- Reject invalid JWKS in client configuration / dependency cleanup and bump (#3603) (1d73d83)
- Restore ability to override auth and token urls for exemplary app (#3590) (dfb129a)
- Return proper error when the grant request cannot be parsed (#3558) (26f2d34)
- Use correct tracer in middleware (#3567) (807cbd2)
Code Generation
- Pin v2.2.0-rc.3 release commit (ad8a4ba)
Features
-
Add more resolution to events and collect client metrics (#3568) (466e66b)
-
Add state override (b8b9154)
-
Add support for OIDC VC (#3575) (219a7c0):
This adds initial support for issuing verifiable credentials
as specified in https://openid.net/specs/openid-connect-userinfo-vc-1_0.html.Because the spec is still in draft, public identifiers are
suffixed withdraft_00. -
Allow to disable claim mirroring (#3563) (c72a316):
This PR introduces another config option called
oauth2:mirror_top_level_claimswhich may be used to disable the mirroring of custom claims into theextclaim of the jwt.
This new config option is an opt-in. If unused the behavior remains as-is to ensure backwards compatibility.Example:
oauth2: allowed_top_level_claims: - test_claim mirror_top_level_claims: false # -> this will prevent test_claim to be mirrored within ext
Closes #3348
-
Bump fosite and add some more tracing (0b56f53)
-
cmd: Add route that redirects to the auth code url (4db6416)
-
Propagate logout to identity provider (#3596) (c004fee):
- feat: propagate logout to identity provider
This commit improves the integration between Hydra and Kratos when logging
out the user.This adds a new configuration key for configuring a Kratos admin URL.
Additionally, Kratos can send a session ID when accepting a login request.
If a session ID was specified and a Kratos admin URL was configured,
Hydra will disable the corresponding Kratos session through the admin API
if a frontchannel or backchannel logout was triggered.- fix: add special case for MySQL
- chore: update sdk
- chore: consistent naming
- fix: cleanup persister
-
Support different jwt scope claim strategies (#3531) (45da11e)
Changelog
- 2c452ef autogen(docs): regenerate and update changelog
- 551c359 autogen(docs): regenerate and update changelog
- 93ebaee autogen(docs): regenerate and update changelog
- 7cfba84 autogen(docs): regenerate and update changelog
- cb64770 autogen(docs): regenerate and update changelog
- 938d4bb autogen(docs): regenerate and update changelog
- 0072ddf autogen(docs): regenerate and update changelog
- c30de7f autogen(docs): regenerate and update changelog
- 6c298b2 autogen(docs): regenerate and update changelog
- a547a74 autogen(docs): regenerate and update changelog
- 5704640 autogen(docs): regenerate and update changelog
- e586cc2 autogen(docs): regenerate and update changelog
- 2bdad2c autogen(docs): regenerate and update changelog
- dc878b8 autogen(docs): regenerate and update changelog
- 425c977 autogen(docs): regenerate and update changelog
- 339bf40 autogen(docs): regenerate and update changelog
- ea40d44 autogen(docs): regenerate and update changelog
- 71d1853 autogen(docs): regenerate and update changelog
- be85c29 autogen(docs): regenerate and update changelog
- 598c21d autogen(docs): regenerate and update changelog
- 42a9615 autogen(docs): regenerate and update changelog
- 330530d autogen(openapi): regenerate swagger spec and internal client
- 254a21b autogen(openapi): regenerate swagger spec and internal client
- ad8a4ba autogen: pin v2.2.0-rc.3 release commit
- 6631c21 autogen: render config schema
- 59ec76b chore(deps): bump semver from 5.7.0 to 5.7.2 (#3569)
- 9fd59e2 chore(deps): bump semver from 5.7.0 to 5.7.2 in /test/e2e/oauth2-client (#3570)
- 3c5c126 chore(deps): bump tough-cookie, @cypress/request and wait-on (#3592)
- 48d5df4 chore: add hperl as codeowner (#3607)
- efd9ca7 chore: bump deps (#3560)
- d5099cb chore: remove fosite branch override (#3599)
- 3914585 chore: replace fosite rewrite (#3564)
- 8ed2a2d chore: support in README (#3565)
- 1a1f504 chore: update repository templates to ory/meta@ac80097
- eb89af7 chore: update repository templates to ory/meta@af28aff
- 4db6416 feat(cmd): add route that redirects to the auth code url
- 749eb8d feat: add
hydra migrate statussubcommand (#3579) - 466e66b feat: add more resolution to events and collect client metrics (#3568)
- b8b9154 feat: add state override
- 219a7c0 feat: add support for OIDC VC (#3575)
- 8eed306 feat: allow Go migrations (#3602)
- 8900cbb feat: allow additional SQL migrations (#3587)
- c72a316 feat: allow to disable claim mirroring (#3563)
- 0b56f53 feat: bump fosite and add some more tracing
- 5bd9002 feat: parallel generation of JSON web key set (#3561)
- c004fee feat: propagate logout to identity provider (#3596)
- 45da11e feat: support different jwt scope claim strategies (#3531)
- 1f1121c fix: add exceptions for internal IP addresses (#3608)
- 9f1c8d1 fix: add kid to verifiable credential header (#3606)
- 6741a49 fix: deflake ttl test
- 01ff9da fix: docker build (#3609)
- 6f592fc fix: enable CORS with hot-reloaded origins (#3601)
- a21e945 fix: only query access tokens by hashed signature
- 1b26c4c fix: racy random string generation (#3555)
- 1d73d83 fix: reject invalid JWKS in client configuration / dependency cleanup and bump (#3603)
- dfb129a fix: restore ability to override auth and token urls for exemplary app (#3590)
- 26f2d34 fix: return proper error when the grant request cannot be parsed (#3558)
- 807cbd2 fix: use correct tracer in middleware (#3567)
Artifacts can be verified with cosign using this public key.
v2.2.0-rc.2
This release optimizes the performance of authorization code grant flows by minimizing the number of database queries. We acheive this by storing the flow in an AEAD-encoded cookie and AEAD-encoded request parameters for the authentication and consent screens.
BREAKING CHANGE:
- The client that is used as part of the authorization grant flow is stored in the AEAD-encoding. Therefore, running flows will not observe updates to the client after they were started.
- Because the login and consent challenge values now include the AEAD-encoded flow, their size increased to around 1kB for a flow without any metadata (and increases linearly with the amount of metadata). Please adjust your ingress / gateway accordingly.
Bug Fixes
- Version clash in apk install (24ebdd3)
Code Generation
- Pin v2.2.0-rc.2 release commit (b183040)
Features
Changelog
- 4194d75 autogen(docs): regenerate and update changelog
- 898aa00 autogen(docs): regenerate and update changelog
- b183040 autogen: pin v2.2.0-rc.2 release commit
- a8ecf80 feat: hot-reload Oauth2 CORS settings (#3537)
- 3ec683d feat: sqa metrics v2 (#3533)
- 24ebdd3 fix: version clash in apk install
Artifacts can be verified with cosign using this public key.
v2.1.2
We are excited to announce the next Ory Hydra release! This release includes the following important changes:
- Fixed a memory leak in the OpenTelemetry implementation, improving overall memory usage and stability.
- Added a missing index for faster janitor cleanup, resulting in quicker and more efficient cleanup operations.
- Fixed a bug related to SameSite in dev mode, ensuring proper functionality and consistency in handling SameSite attributes during development.
We appreciate your continuous support and feedback. Please feel free to reach out to us with any further suggestions or issues.
Bug Fixes
-
Add index on requested_at for refresh tokens and use it in janitor (#3516) (5b8e712)
-
Do not use prepared SQL statements and bump deps (#3506) (31b9e66)
-
sql: Incorrect JWK query (#3499) (13ce0d6):
persister_grant_jwkhad an OR statement without bracket leading to not using the last part of the query.
Code Generation
- Pin v2.1.2 release commit (d94ed6e)
Documentation
Features
Changelog
- 0e84c24 autogen(docs): generate and bump docs
- 9f37172 autogen(docs): regenerate and update changelog
- 872720b autogen(docs): regenerate and update changelog
- 4907223 autogen(docs): regenerate and update changelog
- ba45af0 autogen(docs): regenerate and update changelog
- 3703e5a autogen(docs): regenerate and update changelog
- ca85a17 autogen(docs): regenerate and update changelog
- 0e7e95f autogen(docs): regenerate and update changelog
- be8f726 autogen: add v2.1.1 to version.schema.json
- d94ed6e autogen: pin v2.1.2 release commit
- 20c6fa7 autogen: render config schema
- 400b9af chore(deps): bump @nestjs/core and @openapitools/openapi-generator-cli (#3493)
- f2f007d chore(deps): bump github.com/docker/distribution (#3514)
- b69a332 chore: bump ory/x (#3518)
- cf20054 chore: remove unneeded dependency (#3494)
- e2b7665 chore: update nodemon version for oauth2 client (#3503)
- b71a36b docs: incorrect json output format example (#3497)
- 083d518 feat: add --skip-consent flag to hydra cli (#3492)
- 13ce0d6 fix(sql): incorrect JWK query (#3499)
- 5b8e712 fix: add index on requested_at for refresh tokens and use it in janitor (#3516)
- eddf7f3 fix: disable health check request logs (#3496)
- 31b9e66 fix: do not use prepared SQL statements and bump deps (#3506)
- 5751fae fix: proper SameSite=None in dev mode (#3502)
- 1b1899e fix: sqa config values unified across projects (#3490)
Artifacts can be verified with cosign using this public key.
v2.1.1
We are excited to share this year's Q1 release of Ory Hydra: v2.1!
Highlights:
- Support for Datadog tracing (#3431).
- Ability to skip consent for trusted clients (#3451).
- Setting access token type in the OAuth2 Client is now possible (#3446).
- Revoke login sessions by SessionID (#3450).
- Session lifespan extended on session refresh (#3464).
- Token request hooks added for all grant types (#3427).
- Reduced SQL tracing noise (#3481).
Don't want to run the upgrade yourself? Switch to Ory Network!
Bug Fixes
- Double-hashed access token signatures (#3486) (8720b25), closes #3485
- Reduce SQL tracing noise (#3481) (6e1f545)
Code Generation
- Pin v2.1.1 release commit (6efae7c)
Changelog
- df16a26 autogen(docs): generate and bump docs
- ed2ac06 autogen(docs): regenerate and update changelog
- 6078f85 autogen(docs): regenerate and update changelog
- ddfbd65 autogen: add v2.1.0 to version.schema.json
- 6efae7c autogen: pin v2.1.1 release commit
- ad549d6 autogen: pin v2.1.1 release commit
- 2f7cda5 autogen: render config schema
- 0448284 chore: update ory/x (#3480)
- 8720b25 fix: double-hashed access token signatures (#3486)
- 6e1f545 fix: reduce SQL tracing noise (#3481)
Artifacts can be verified with cosign using this public key.
v2.1.0
We are excited to share this year's Q1 release of Ory Hydra: v2.1.0!
Highlights:
- Support for Datadog tracing (#3431).
- Ability to skip consent for trusted clients (#3451).
- Setting access token type in the OAuth2 Client is now possible (#3446).
- Revoke login sessions by SessionID (#3450).
- Session lifespan extended on session refresh (#3464).
- Token request hooks added for all grant types (#3427).
- Reduced SQL tracing noise (#3481).
Don't want to run the upgrade yourself? Switch to Ory Network!
Bug Fixes
Code Generation
- Pin v2.1.0 release commit (3649832)
Changelog
- 5c2e227 autogen(docs): regenerate and update changelog
- 3649832 autogen: pin v2.1.0 release commit
- 6e1f545 fix: reduce SQL tracing noise (#3481)
Artifacts can be verified with cosign using this public key.
v2.1.0-pre.2
autogen: pin v2.1.0-pre.2 release commit
Code Generation
- Pin v2.1.0-pre.2 release commit (3b1d87e)
Changelog
- 3b1d87e autogen: pin v2.1.0-pre.2 release commit
Artifacts can be verified with cosign using this public key.
v2.1.0-pre.1
autogen: pin v2.1.0-pre.1 release commit
Code Generation
- Pin v2.1.0-pre.1 release commit (2289e6b)
Changelog
- 2289e6b autogen: pin v2.1.0-pre.1 release commit
- 0d740d9 chore(deps): bump github.com/opencontainers/runc from 1.1.4 to 1.1.5 (#3476)
- c29b968 chore: update alpine version
Artifacts can be verified with cosign using this public key.
v2.0.3
Bugfixes for migration and pagination regressions and a new endpoint.
Bug Fixes
-
Add
client_idandclient_secrettorevokeOAuth2Token(#3373) (93bac07) -
Docker build (48217bd)
-
Invalidate tokens with inconsistent state (#3385) (542ea77), closes #3346:
This patch includes SQL migrations targeting environments which have not yet migrated to Ory Hydra 2.0. It removes inconsistent records which resolves issues during the migrations process. Please be aware that some users might be affected by this change. They might need to re-authorize certain apps. However, most active records should not be affected by this.
Installations already on Ory Hydra 2.0 will not be affected by this change.
-
No longer auto-generate system secret (c5fe043):
This patch changes Ory Hydra's behavior to no longer auto-generate a temporary secret when no global secret was set. The APIs now return an error instead.
See ory/network#185
-
Prevent multiple redirections to post logout url (#3366) (50666b9), closes #3342
Code Generation
- Pin v2.0.3 release commit (16831c5)
Features
Changelog
- 5d79e57 autogen(docs): generate and bump docs
- bd19086 autogen(docs): regenerate and update changelog
- 2720839 autogen(docs): regenerate and update changelog
- a400a35 autogen(docs): regenerate and update changelog
- 6710ddc autogen(docs): regenerate and update changelog
- d7a28e9 autogen(docs): regenerate and update changelog
- f2925ee autogen(docs): regenerate and update changelog
- 2986605 autogen(docs): regenerate and update changelog
- c586e03 autogen(openapi): regenerate swagger spec and internal client
- c65342e autogen: add v2.0.2 to version.schema.json
- 16831c5 autogen: pin v2.0.3 release commit
- b28bad3 chore(deps): bump decode-uri-component in /test/e2e/oauth2-client (#3377)
- cb23cca chore(deps): bump minimatch in /test/e2e/oauth2-client (#3381)
- 93fc0a1 chore(deps): bump qs from 6.5.2 to 6.5.3 (#3380)
- 316b582 chore(deps): bump qs, body-parser and express in /test/e2e/oauth2-client (#3379)
- f9f0337 chore: list contributors in file (#3345)
- d275ad6 feat: list consent sessions by session id (#2853)
- 93bac07 fix: add
client_idandclient_secrettorevokeOAuth2Token(#3373) - 48217bd fix: docker build
- 4ee4456 fix: introspect command CLI example (#3353)
- 542ea77 fix: invalidate tokens with inconsistent state (#3385)
- c5fe043 fix: no longer auto-generate system secret
- 50666b9 fix: prevent multiple redirections to post logout url (#3366)
- 3831b44 fix: strip
publicfrom schema (#3374) - e8d8de9 fix: token pagination (#3384)
Artifacts can be verified with cosign using this public key.
v2.0.2
This release resolves bugs and SDK publishing issues.
Bug Fixes
-
Correct migration file name (01f80a8)
-
Incorrect consent removal on authentication revokation (ccf2388):
This patch resolves a regression where, in a certain condition, an accepted consent could be incorrectly deleted when the related authentication session was removed.
-
Isolate transactions for crdb (f22046f)
-
Scope type should be string instead of int (#3337) (f59f1c6):
Closes ory/sdk#223
Code Generation
- Pin v2.0.2 release commit (ce96826)
Documentation
- Add refresh token grant type (c752125)
- Fix typo (dcfd11f)
- Standardize license headers (#3216) (d768cf6)
- Update README link (6184b6a)
Features
Tests
Changelog
- 94aadf8 autogen(docs): generate and bump docs
- 0eeea90 autogen(docs): regenerate and update changelog
- 8d92030 autogen(docs): regenerate and update changelog
- 48603ba autogen(docs): regenerate and update changelog
- bedaf48 autogen(docs): regenerate and update changelog
- 3749a73 autogen(docs): regenerate and update changelog
- cec489f autogen(docs): regenerate and update changelog
- d37b323 autogen(docs): regenerate and update changelog
- cdfcf45 autogen(docs): regenerate and update changelog
- 70e6fe9 autogen(docs): regenerate and update changelog
- 4fd6baa autogen(docs): regenerate and update changelog
- fd02049 autogen(openapi): regenerate swagger spec and internal client
- 74d4569 autogen(openapi): regenerate swagger spec and internal client
- 164f4b5 autogen: add v2.0.1 to version.schema.json
- ce96826 autogen: pin v2.0.2 release commit
- 80a1335 chore: license checker (#3328)
- f8a7ced chore: remove obsolete header (#3334)
- 90152fa chore: update Ory CLI with breaking changes to the format task (#3338)
- 0b32280 chore: update repository templates to ory/meta@852a1ae
- cda9fd4 chore: update repository templates to ory/meta@a2fba7e
- 5418433 chore: update repository templates to ory/meta@b41b1ee
- 736aaef chore: update repository templates to ory/meta@d3f8710
- c752125 docs: add refresh token grant type
- dcfd11f docs: fix typo
- d768cf6 docs: standardize license headers (#3216)
- 6184b6a docs: update README link
- 16bd568 feat: enable simultaneous auth flows by creating client related csrf co… (#3059)
- c54b9db fix: add v2 suffix (#3340)
- 01f80a8 fix: correct migration file name
- ccf2388 fix: incorrect consent removal on authentication revokation
- 729102f fix: incorrect jwk import order (#3344)
- f22046f fix: isolate transactions for crdb
- f59f1c6 fix: scope type should be string instead of int (#3337)
- c417be1 test: fix flaky test
- 643e88c test: resolve time race
Artifacts can be verified with cosign using this public key.