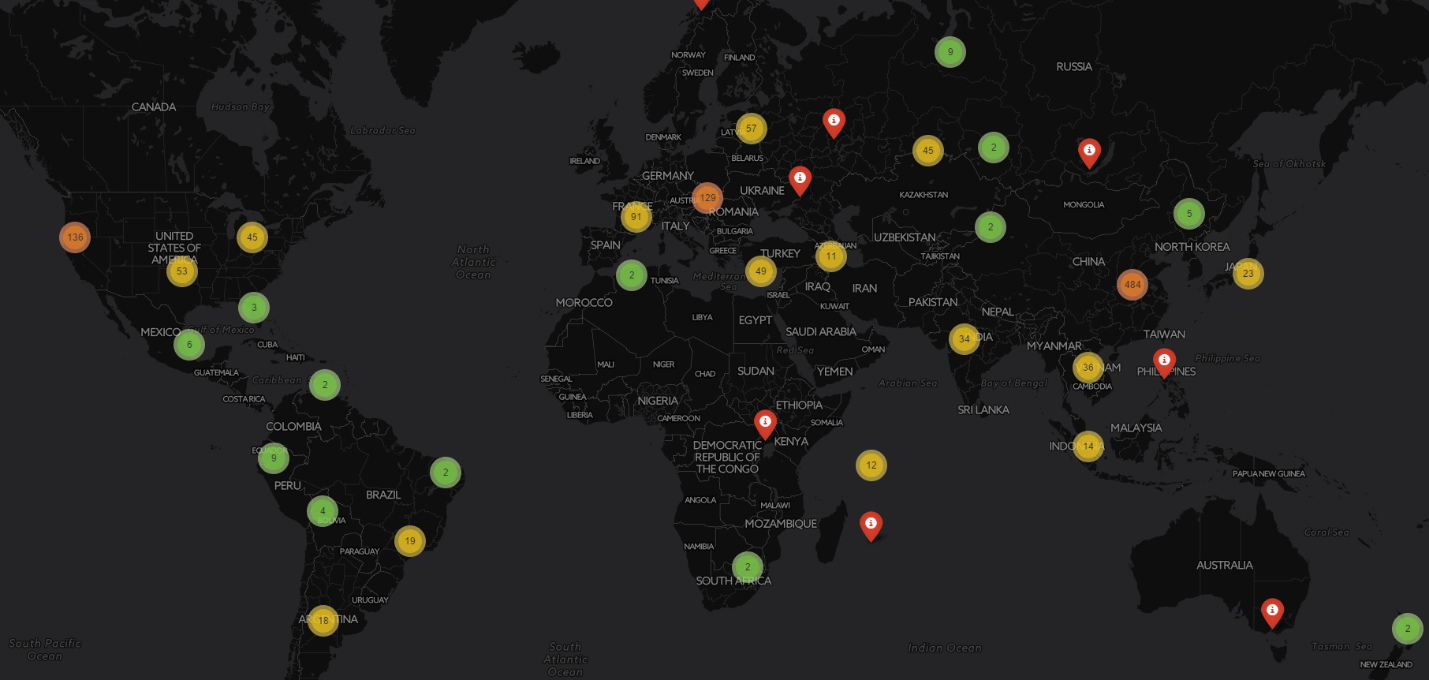
OpenPiMap is an open source NetFlow protocol analyzer written entirely in Python 3 designed to provide insights on botnet and network traffic analysis in a small business or home network. It was designed and tested on a Windows 10 computer and then ran continuously on a Raspberry Pi 1 Model B (and should work flawlessly on a Pi2 or Pi3). The netflow_collector.py is designed to be run in the background (as a cron job) continuously and will listen for NetFlow v5 traffic (generated by PfSense, Cisco, etc.). The openipmap.py script can be run daily, weekly, or as needed. There are lots of incomplete and commented features so be sure to follow the code to see what it is doing. The script is designed to follow this path:
- Parse NetFlow data retrieved from the netflow_collector.py script.
- Retrieve multiple IP blacklists and determine the public IP address of the host that it is running on. (Or can be hardcoded for running offline)
- Correlate inbound and outbound IP addresses and potentially malicious IP addresses, ports, etc. to determine any kind of "bad" activity.
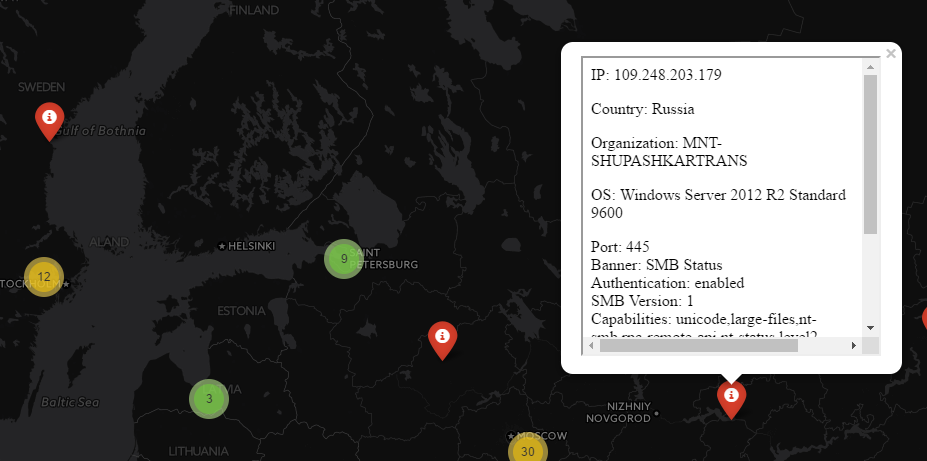
- For every IP address that is identified as suspicious, it will query Shodan.io for current services, hostname, etc. This can be immensely useful in determining if the device is part of a botnet, an IoT device, or other infected system on the internet. All of this data can then be used for trend analysis, reporting, incident tracking, etc.
- Finally, the script saves the map as an HTML file and pushes out an SMS message with the number of "bad" IPs that were detected.
The script has built in functionality to do data consumption statistics, top ports/services charts, and 24 hour / weekly / monthly queries. However, Shodan.io has a rate limit on their free API usage!! Looking up hundreds or thousands of unique IPs will take a LONG time!! This doesn't break anything.. but be prepared to wait a few hours if you are running monthly reports.
The code isn't quite complete. However, it has been running for 6+ months on my Raspberry Pi 1 Model B without any hiccups. Be sure to check out the API keys required for Shodan and Twilio functions to work (all requests are well within the free API limits). You will also need a local copy of the GeoIP database for offline geolocation of IP addresses.
Credit goes to Lalit Patel (http://codestacking.blogspot.com/2017/02/netflow-version-5-collector-in-python.html) for the NetFlow Collector. I made a few changes required to save the raw data to a CSV file for later processing and logging, but his collector was a great place to start.