Use this CDK stack to create a security group for bastion host.
- A security group acts as a virtual firewall for your instance to control inbound and outbound traffic.
- A network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets.
- Comparison of security groups and network ACLs
- Deploy a security group for bastion host.
- Add inbound rules for ssh access.
You will need the following before utilize this CDK stack:
- AWS CLI
- AWS Account and User
- Node.js
- IDE for your programming language
- AWS CDK Tookit
- AWS Toolkit VSCode Extension
Define project-name and env context variables in cdk.json
{
"context": {
"project-name": "container",
"env": "dev",
"profile": "devopsrepo"
}
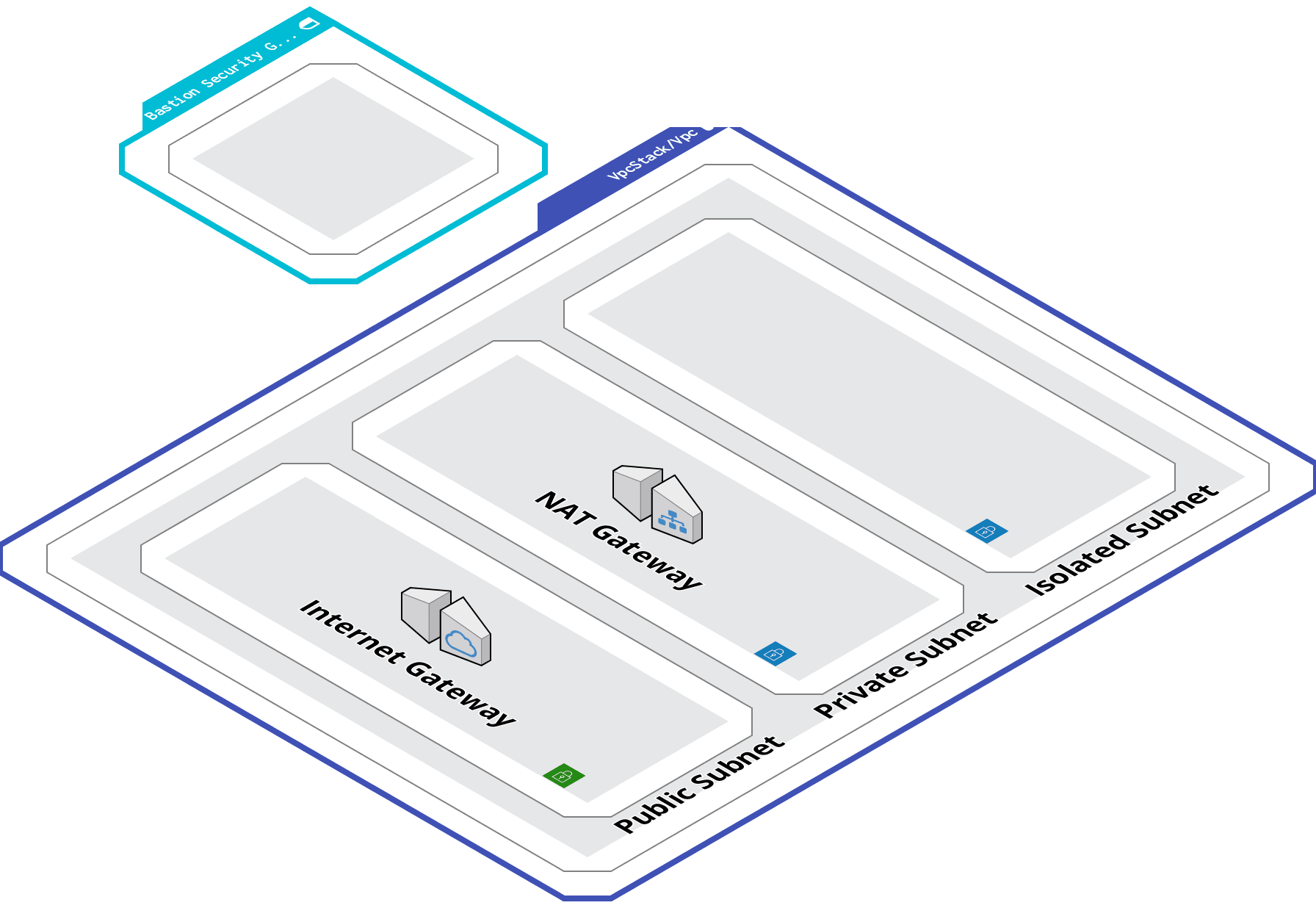
}Setup standard VPC with public, private, and isolated subnets.
const vpc = new ec2.Vpc(this, 'Vpc', {
maxAzs: 3,
natGateways: 1,
cidr: '10.0.0.0/16',
subnetConfiguration: [
{
cidrMask: 24,
name: 'ingress',
subnetType: ec2.SubnetType.PUBLIC,
},
{
cidrMask: 24,
name: 'application',
subnetType: ec2.SubnetType.PRIVATE,
},
{
cidrMask: 28,
name: 'rds',
subnetType: ec2.SubnetType.ISOLATED,
}
]
});- maxAzs - Define 3 AZs to use in this region.
- natGateways - Create only 1 NAT Gateways/Instances.
- cidr - Use '10.0.0.0/16' CIDR range for the VPC.
- subnetConfiguration - Build the public, private, and isolated subnet for each AZ.
Create flowlog and log the vpc traffic into cloudwatch
vpc.addFlowLog('FlowLog');Get vpc create from vpc stack
const { vpc } = props;Create security group for bastion host
const bastionSecurityGroup = new ec2.SecurityGroup(this, 'BastionSecurityGroup', {
vpc: vpc,
allowAllOutbound: true,
description: 'Security group for bastion host',
securityGroupName: 'BastionSecurityGroup'
});- vpc - Use vpc created from vpc stack.
- allowAllOutbound - Allow outbound rules for access internet
- description - Description for security group
- securityGroupName - Define the security group name
Allow ssh access to bastion host
bastionSecurityGroup.addIngressRule(ec2.Peer.anyIpv4(), ec2.Port.tcp(22), 'SSH access');Deploy all the stacks to your aws account.
cdk deploy '*'
or
cdk deploy '*' --profile your_profile_nameAct as a firewall to block all inbound traffic and allow the only necessary port to access the instances.
npm run buildcompile typescript to jsnpm run watchwatch for changes and compilenpm run testperform the jest unit tests
cdk list (ls)Lists the stacks in the appcdk synthesize (synth)Synthesizes and prints the CloudFormation template for the specified stack(s)cdk bootstrapDeploys the CDK Toolkit stack, required to deploy stacks containing assetscdk deployDeploys the specified stack(s)cdk deploy '*'Deploys all stacks at oncecdk destroyDestroys the specified stack(s)cdk destroy '*'Destroys all stacks at oncecdk diffCompares the specified stack with the deployed stack or a local CloudFormation templatecdk metadataDisplays metadata about the specified stackcdk initCreates a new CDK project in the current directory from a specified templatecdk contextManages cached context valuescdk docs (doc)Opens the CDK API reference in your browsercdk doctorChecks your CDK project for potential problems