VISE is a search engine on information delivered by OSINT sources (e.g. NVD, Exploit DB) to support Vulnerability Assessment.
The information can be exctracted by:
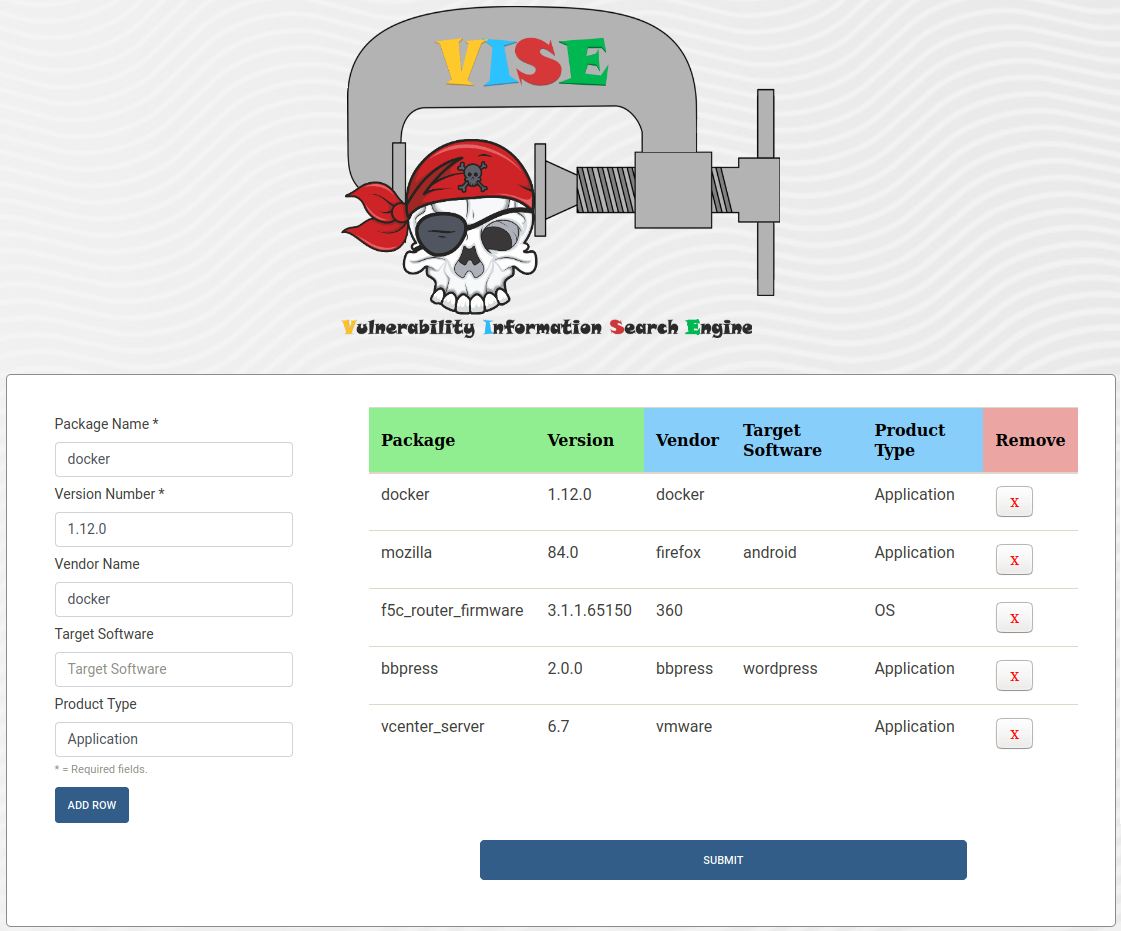
1) manually filling a form:
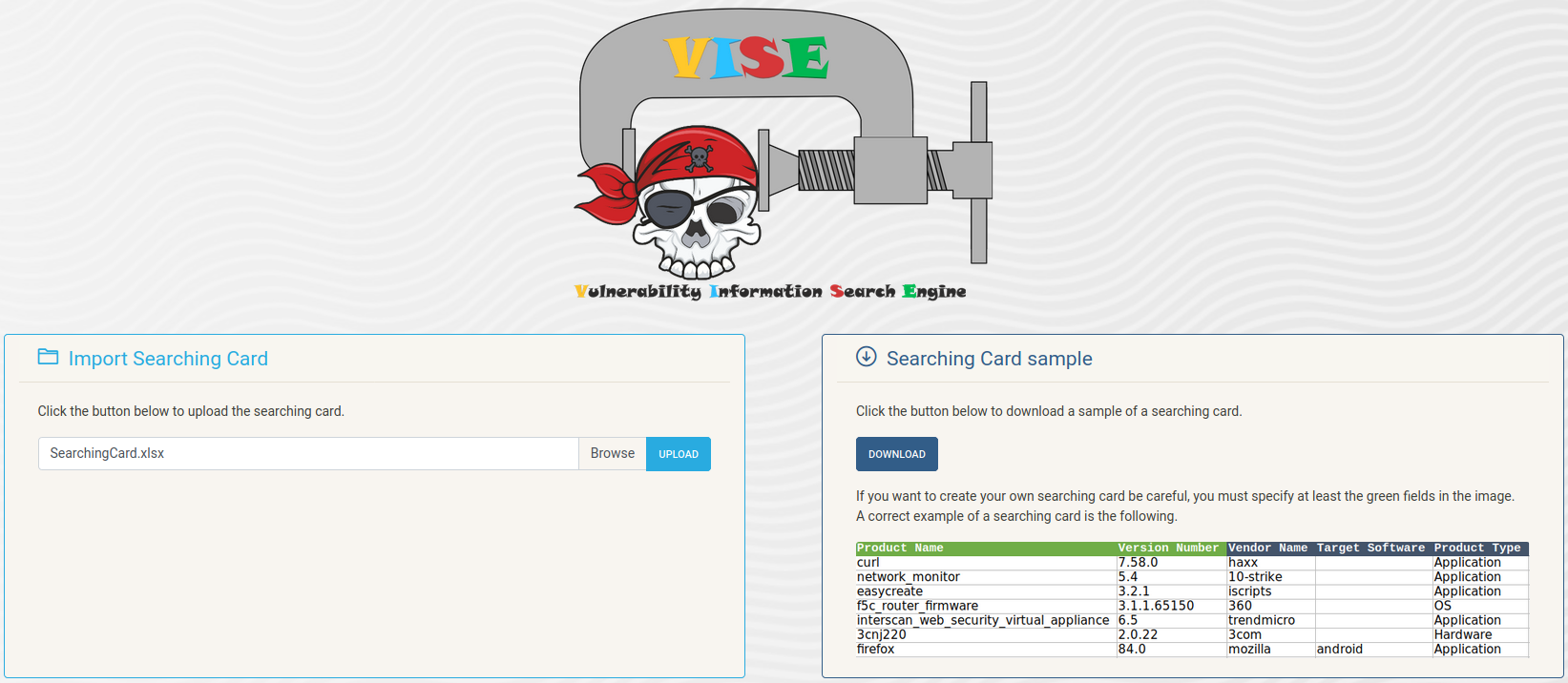
2) uploading a searching card:
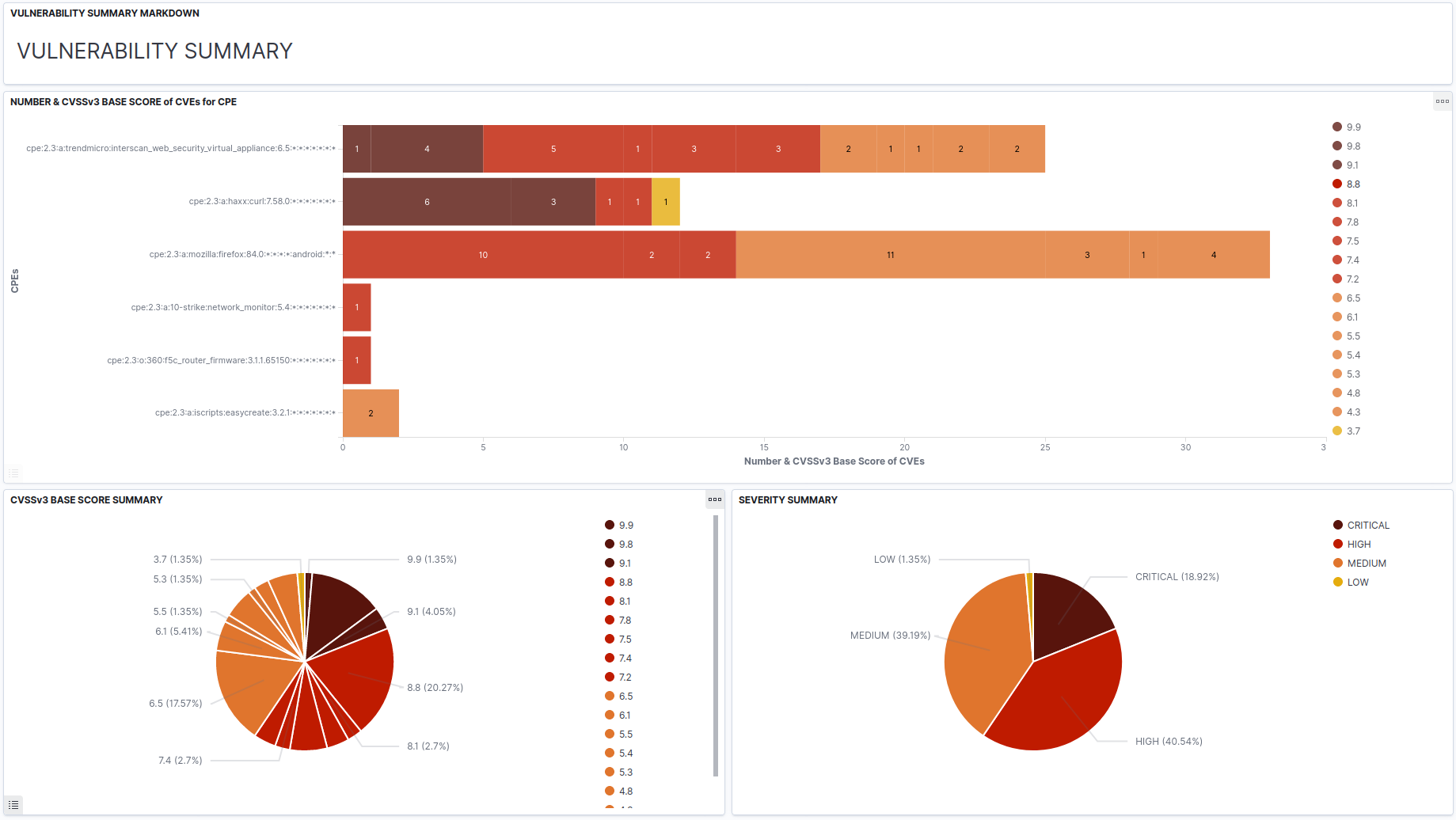
As a result, in both cases can be obtained three dashboards hosted on Kibana, describing respectivelly:
- a summary on found vulnerabilities:
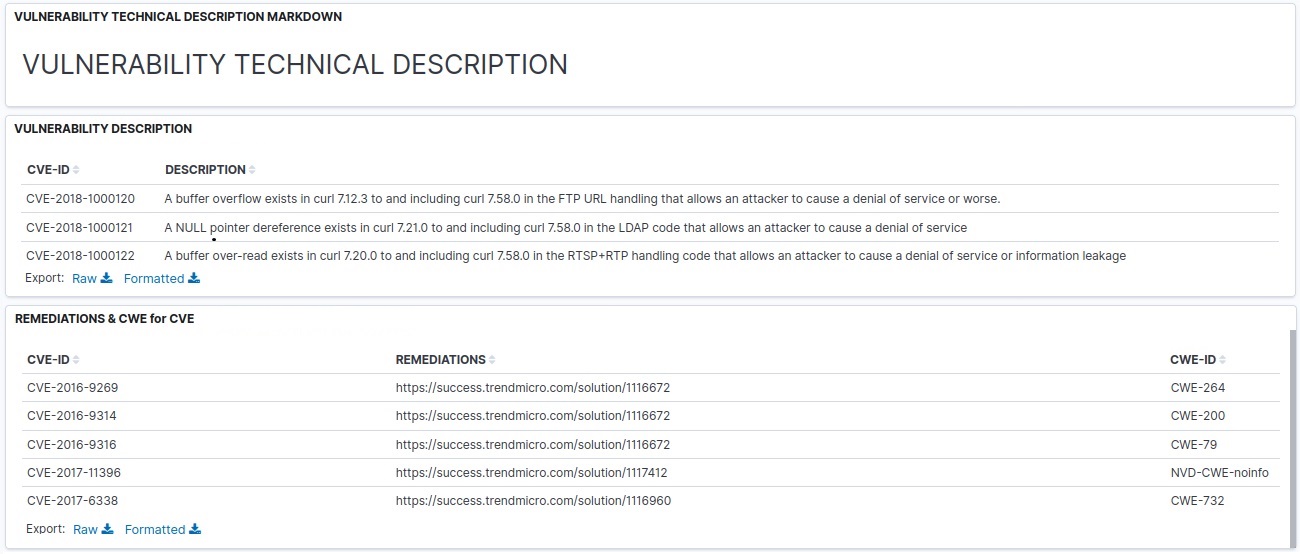
- a more deep description about ones:
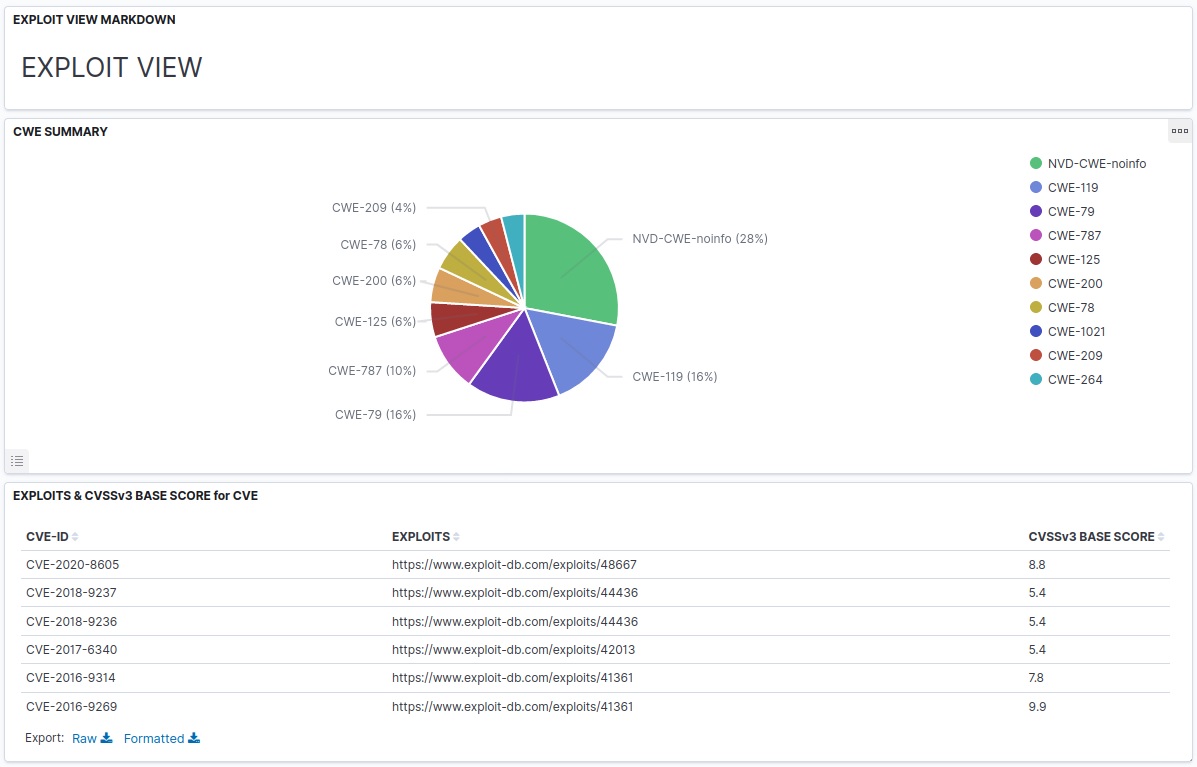
- the available exploits for them:
Moreover, it is possible to export those kinds of data as a unified CSV so that they can be easily managed and reviewed.
VISE can be also used from the CLI running the following commands:
cd VISE/VISE_app/
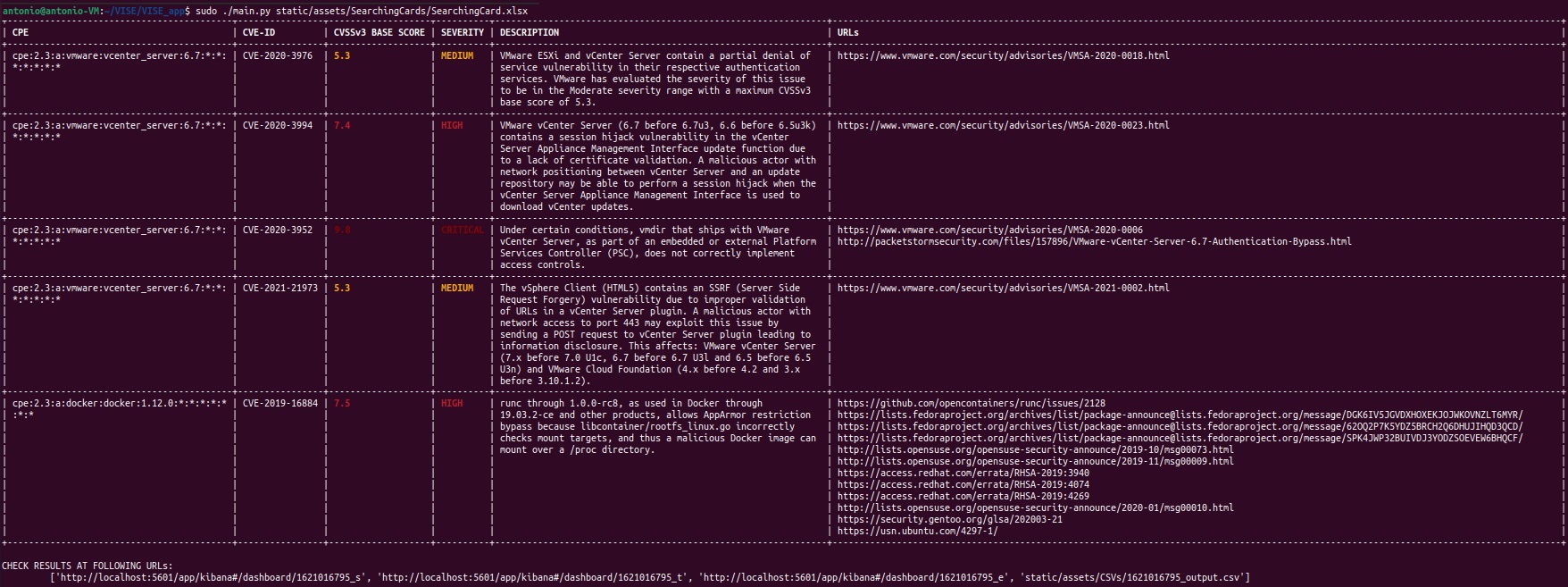
sudo ./main.py static/assets/SearchingCards/SearchingCard.xlsx
- Linux distribution (Ubuntu preferred)
- python3-pip, python3-venv
cd VISE/scripts/
sudo ./installOthers.sh
- flask
cd ../VISE_app/
source venv/bin/activate
sudo ../scripts/installFlask.sh
- exploitdb
sudo ../scripts/installExploitDB.sh
searchsploit -u
sudo cve_searchsploit -u
- docker
sudo ../scripts/installDockerUbuntu.sh
(the script also start Kibana and Elasticsearch containers with docker-compose)
(kibana starts at http://localhost:5601)
(the username is "elastic", the password is "changeme")
- upload indices in elasticsearch
sudo ../scripts/uploadIndices.sh
- start VISE
cd VISE/VISE_app/
sudo ../scripts/startVISE.sh
Antonio Forte |
Salvatore Scotto di Perta |
fabiom95 |
glkhan |
Giuseppe Siani |
This project is under the MIT license
If you use this tool in your academic work you can cite it using:
@misc{vise,
author = {Antonio Forte},
howpublished = {GitHub},
month = apr,
title = {{VISE (Vulnerability Information Search Engine)}},
year = {2020},
url = {https://github.com/antonioforte1995/VISE},
}