A visualization tool that can extract information from any server log (i.e. HTTP server/Django/Auth/etc), reverse-search the data, and visualize the origination of the authentication attempts.
The following information are extracted from the logs:
- IP Address
- Port Number
- Username
- Server Message
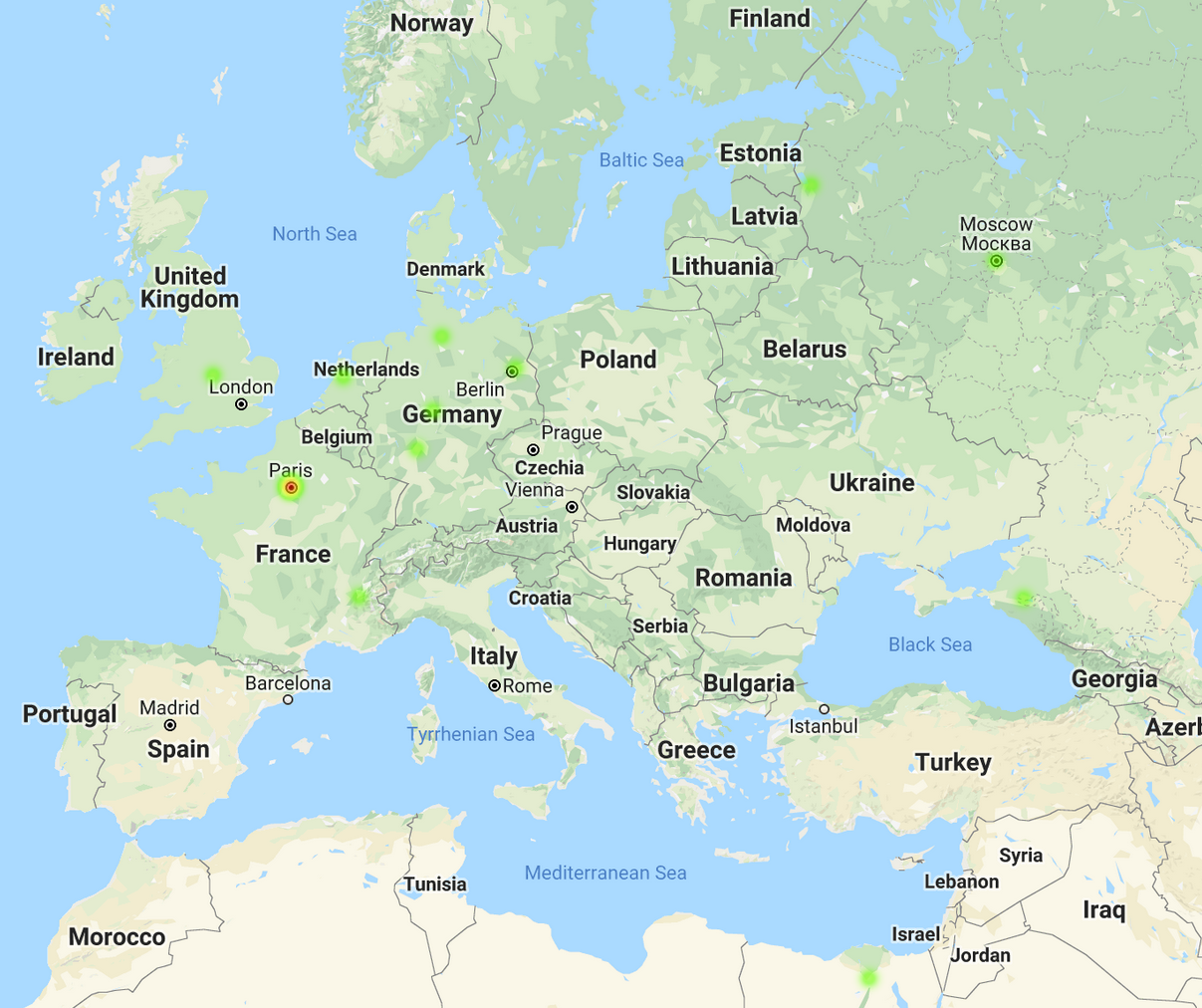
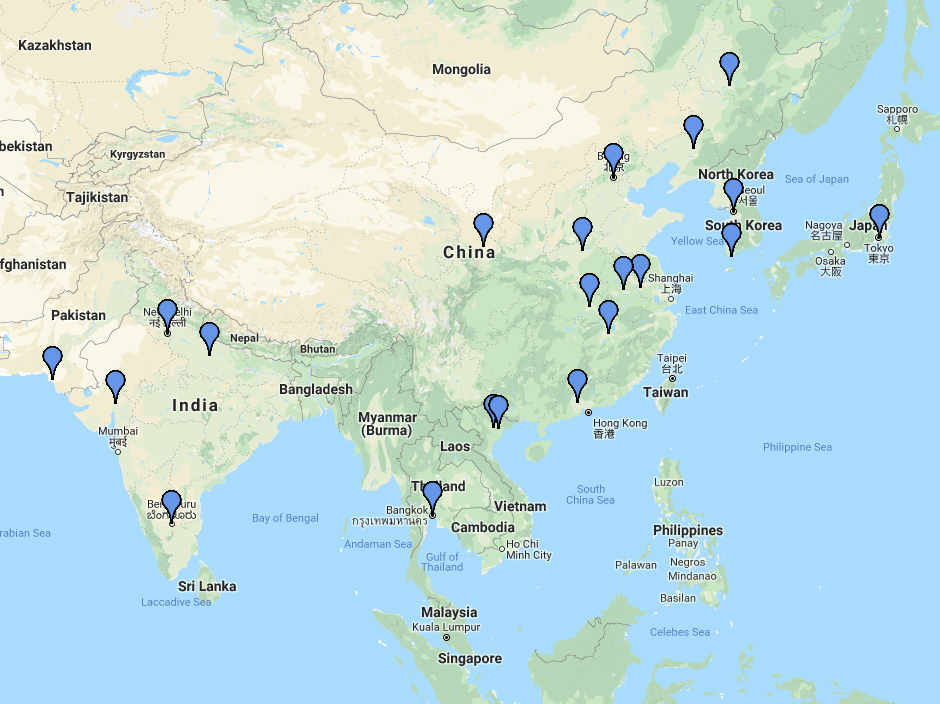
Once the information is extracted, each IP from the authentication attempt is checked with Shodan to get it's location data. An HTML page is created with a map and pins (associated to each IP).
Here is a sample of the data on a heat map:
Here is a sample of the data with markers on a map:
**This project is also a Python Package now via PyPi ().
The following functionality are currently available from Authr:
- Create a CSV from server logs
- Create an html heat map from the server logs
- Create an html scatter map from the server log data
- Create an html map with markers from the server log data
- Create an html map with a polygon plot (connecting lines to each point) from the server log data
These instructions will get you a copy of the project up and running on your local machine. You will be able to scrape your own server logs.
This tool heavily relies on Shodan (search engine for Internet-connected devices) to find the location of an IP address.
Go here to sign up for an account and get an developer API key.
The following steps go through installing Python dependencies and setting up the environment for the tool.
- Install the Python modules for this tool
$ cd Authr $ pip install -r requirements.txt - (Optionally) Install VirtualEnv to setup a separate Python environment for the project.
$ pip install virtualenv $ virtualenv venv $ source venv/Scripts/activate
Below is a code sample on how to generate a heat map and csv from your server log:
- Place the following in a python file
import authr, argparse, os def main(): parser = argparse.ArgumentParser(description='Scrape Server Logs and Inserted into the DB') parser.add_argument('-a', '--auth', help='Server Log', required=True) parser.add_argument('-k', '--key', help='Shodan Key', required=True) args = vars(parser.parse_args()) log_file_path = args['auth'] shodan_api_key = args['key'] full_path = os.path.dirname(os.path.abspath(__file__)) full_log_file_path = full_path + log_file_path authr.set_shodan_api_environment(shodan_api_key) marker_list = authr(full_log_file_path).parse_auth_log(full_log_file_path) authr.create_authr_map_with_heatmap_plots(marker_list, "example_map.html") authr.create_authr_csv(marker_list, "example-csv.csv") if __name__ == "__main__":`` main() - Run the following command
$ python test.py -a {__path_to_server_log_file__} -k {__Shodan_API_Key__}
You can also run the authr.py file by itself, and provide arguments to what functionality you would like to use.
$ python authr.py -a {__path_to_server_log_file__} -k {___Shodan_API_Key__}Command Line / Terminal Arguments:
- -a (Authentication File)
- -k (Shodan API Key)
- -f (Filename of your output file (also provide path))
- -hm (Generate a heat map)
- -c (Generate a csv)
- -s (Generate a scatter plot map)
- -p (Generate a polygon plot map)
- -m (Generate a marker plot map)
Sample command to generate a heat map:
$ python authr.py -a \\example-logs\\auth-01-14-2018.log -k {___Shodan_API_Key__} -f example-map.html -hm
- Python 3.6
- Shodan - Search engine API for Internet-connected devices.
- GMPLOT - Used to generate maps with pins for the location of authentications.
This tool was created out of my interest regarding the amount of SSH authentication attempts made on one of my personal Linux servers. I was curious at where the attempts were coming from, and decided to scrape and reverse search the IP addresses from the auth logs. This became more of a research project to figure out where and how attackers found my personal server.
- Jimmy Le - Jldevops
Licensed under the MIT License